How to hack your way into RSTA drivers test
Or atleast how you can take advantage of RSTA drivers booking's vulnerable code.
I didn’t have a drivers license until 2 months ago. I had had my learners for around 2 years but never got around to actually taking the test because of 2 reasons. One, the timings never matched, I was home for short while then had to leave and secondly when I did come back home for the longest time, the drivers registration was always booked.
The only time I could “legally” get through the waiting list was when I decided to take it in Bumthang but I failed it miserably (even failed the theory test). After this failed test I couldn’t bother to request for another leave from work and then travel by bus for 8 hours to Bumthang to just do a frickin drivers test. So, I decided to see if I could exploit any loophole in the RSTA booking system and, with the help of Nuchu, we did do it.
Thats enough for the backstory I’ll first go into how to do it (if your’e just here for that) and then into why it works.
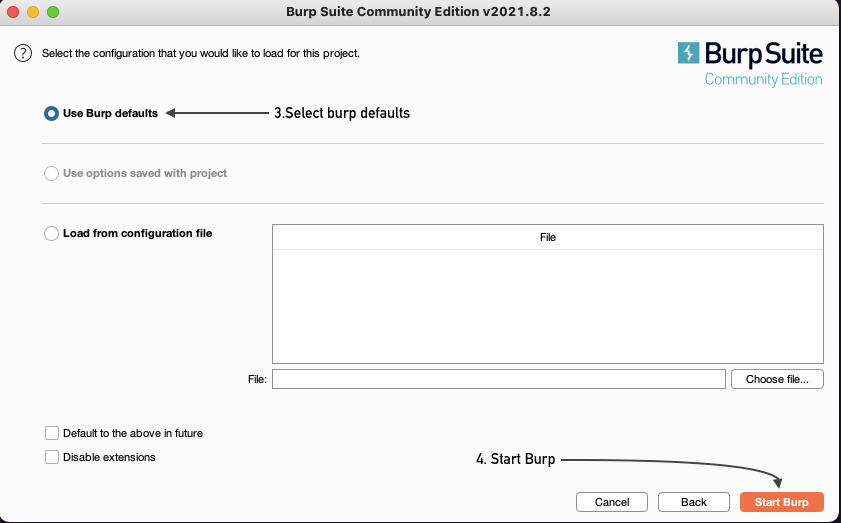
Step 1: Download Burp
Download this software first: Burp . We will use this to change the API response from RSTA. After youre done installing it open up the application.
Just check the application defaults and you should be fine (see pics for directions).
After running start you should be routed to the burp app page. On this part just go to the proxy tab in the headers tab and then click on open browser inside of “Burp’s Embedded Browser” card. Refer to pic for screenshots. This just opens up a chromium browser with burp configured so as to not have to config things.
Step 2: Disabling the simple validations
After opening up the browser, route to the drivers test booking site. Fill in your license details and select a test date. If the test date isn’t full then congrats you can book it without having to do all of this. Even if it is full though, no worries. After you’ve entered your details and selected a test date, if the test date is packed then you should be shown this screen.
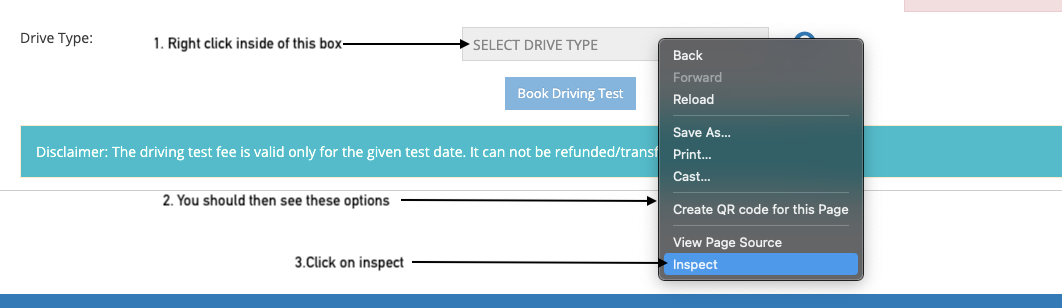
After getting on this screen what you need to do is right click on the selection input called “SELECT DRIVE TYPE” and then you should see some options to tinker with as shown below. From the options choose inspect.
Once you click on inspect you will see a bunch of HTML right below or might be on the side. But this line of code should be highlighted
<select name="drivetype" onchange="getDriveTypeTestMarks(this.value)" id="DRIVE_TYPE" class="form-control" disabled="disabled"><option value="">SELECT DRIVE TYPE</option></select>now what you need to do is just remove the disabled=”disabled” which will result in this line rather than the above:
<select name="drivetype" onchange="getDriveTypeTestMarks(this.value)" id="DRIVE_TYPE" class="form-control"><option value="">SELECT DRIVE TYPE</option></select>and then press enter. That should allow you to choose the vehicle type.
Now you just select one of the options and hit book driving test.
Step 3: Intercepting and changing the response with Burp
Now you should see the confirmation screen, check the I accept terms and conditions. But before you press on yes. Go back to your burp screen and turn on the interceptor. All you need to do is just click on it.
Now once you’ve turned on the interceptor, accepted the terms and conditions, press on that yes button. There wont be anything dramatic. But don’t do anything on the browser instead go to your burp screen and you should see this.
Now what you do is click on action and then you should see a bunch of options. Go down to Do intercept and press on response to this request.
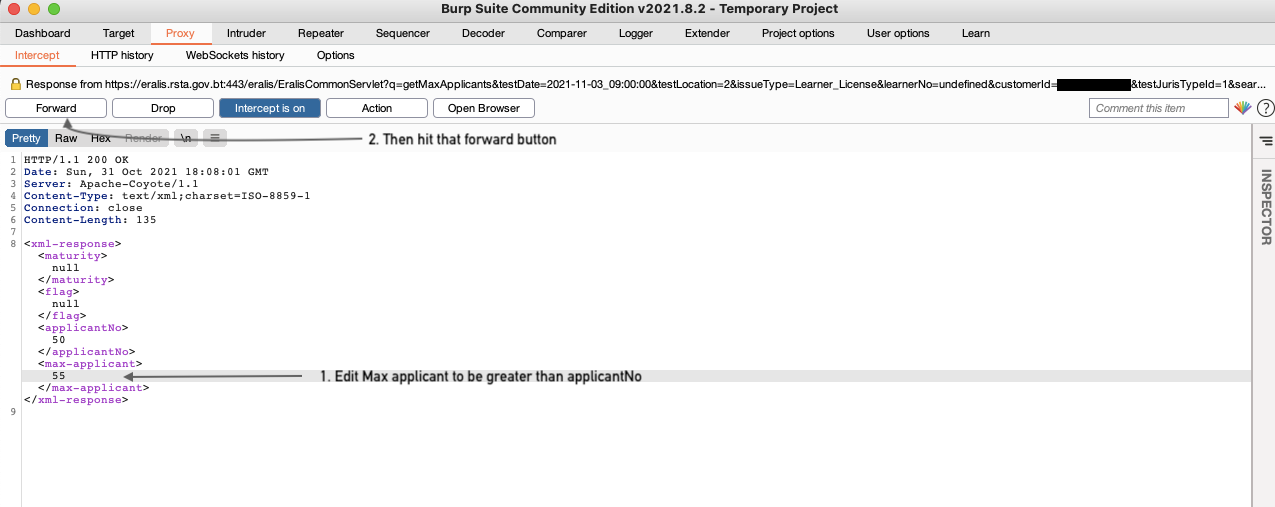
This wont do anything right now but after finishing all of the above steps click on forward
You will then see a type of screen like below although the numbers for max applicant and applicant no might be different.
Now edit the max applicant to be greater than the applicant no. So maybe to something like below. and then press on forward after you’re done.
You’re now done by passing their security another screen will pop up on burp but you don’t have to do anything for that, instead turn the interceptor off and you’re good. Wait for a bit and you will be shown the screen for payment and once you pay it out congrats you’ve booked your drivers test!!
Thats all for the hack, the following sections are going to explore into why exactly all of this works.
So WhY DoEs tHiS WoRK?¿?
Let’s examine why exactly this hack works. Im not too sure but the application might be built in PHP and is rendered on server side. That doesn’t have anything to do with the vulnerability though. I just wanted to mention it. The loophole seems to be in the response of the API requests and their validations. When first hitting on that submit button, after youve entered your learner license details, you get back an XML response with the script for the validation.
This is the request:
https://eralis.rsta.gov.bt/eralis/service.html?method=learnerLicenseDetails&learnerNo=G/LL-12341&cid=123412234123&testType=&form_type=book_driving_test&issueType=&issueBasedOn=Learner_LicenseThe response of this request has these 2 functions in the script: getMaxApplicants(verifyType) where verifyType is given the value ‘BOOK_DRIVE_TEST’ to book the driving test as well. getMaxApplicants checks the response from the getMaxApplicants API call: the one which we edited above. It foregoes validation only if this condition is not met:
if(parseInt(applicantNo) >= parseInt(maxApplicant))
and since we have edited the applicantNo to be less than the maxApplicant. In our case above we edited maxApplicant to be 55 where as applicant number was 50 so this response by passes the validation. Since its passed all validation it then goes into this function defined in their script:
if(verifyType=="BOOK_DRIVE_TEST") { bookDrivingTest();}Ans since verify type is ‘BOOK_DRIVE_TEST’ it then runs the function bookDrivingTest(); This function again checks the validation but since we already passed it once, we pass it again and then it calls the post request to book the drivers test
type : "POST",
url:"/eralis/service.html?method=bookDrivingTest&issueType="+issueType+"&cid="+cid+"&learnerNo="+learnerNo+"&testType="+testType+"&issueBasedOn="+issueBasedOnAnd here lies the issue. They’ve kept the maxApplicant validation only on the front end side but when triggering this POST request they don’t seem to run validations on their backend side. So technically if you knew all the details that need to be sent in this POST request you could just hit it with Postman and you’d be able to save your booking. But the issue will be that you wont be able to access the payment portal. Alright thats all!